How to Install Focalboard on CentOS 9 Stream
-
by cobra_admin
- 58
Introduction
Focalboard is a free, open-source collaboration and productivity tool that lets you organize and manage projects. This article explains how to install Focalboard on a CentOS 9 Stream server.
Prerequisites
- Launch a new CentOS 9 Stream server on Vultr.
- Create a DNS “A” record pointing to the server’s IP address, like
board.example.com. - Log in to the server with SSH as a non-root user with sudo privileges.
- Install PostgreSQL.
- Install Nginx.
Create the Focalboard Database
- Log in to PostgreSQL.
$ sudo -iu postgres psql - Create a new database.
# CREATE DATABASE focalboardb; - Set up a new database user with a strong password.
# CREATE USER exampleuser WITH PASSWORD 'choose_a_strong_password'; - Grant the user rights to use the database.
# GRANT ALL PRIVILEGES ON DATABASE focalboardb TO exampleuser; - Exit PostgreSQL.
# \q
Installation
- Download the latest Focalboard release file.
Latest=$(curl -s https://api.github.com/repos/mattermost/focalboard/releases/latest|grep tag_name | cut -d '"' -f 4) wget https://github.com/mattermost/focalboard/releases/download/${Latest}/focalboard-server-linux-amd64.tar.gz - Extract files from the archive.
$ tar -xvf focalboard-server-linux-amd64.tar.gz - Move the extracted files to
/opt.$ sudo mv focalboard /opt/ - Change to the Focalboard directory.
$ cd /opt/focalboard/ - Using a text editor of your choice, edit the
config.jsonfile.$ sudo nano config.json - Find the following lines:
"dbconfig": "./focalboard.db", "postgres_dbconfig": "dbname=focalboard sslmode=disable", - Change them to reflect your Postgres database as shown below. Change
exampleuserandchoose_a_strong_passwordto the values you set in the first section."dbtype": "postgres", "dbconfig": "postgres://exampleuser:choose_a_strong_password@localhost/focalboardb?sslmode=disable&connect_timeout=10", - Save and close the file.
- Copy
config.jsonto/opt/focalboard/bin.$ sudo cp /opt/focalboard/config.json /opt/focalboard/bin/ - Copy the
packdirectory to/opt/focalboard/bin.$ sudo cp -r /opt/focalboard/pack /opt/focalboard/bin/ - Verify the system SELinux mode.
$ sudo getenforce - Set the SELinux mode from enforcing to permissive.
$ sudo setenforce 0
Configure Nginx as a Reverse Proxy
- Create a new Nginx configuration file.
$ sudo touch /etc/nginx/conf.d/board.example.com.conf - Edit the file.
$ sudo nano /etc/nginx/conf.d/board.example.com.conf - Copy and paste the following configurations to the file. Replace
board.example.comwith the DNS “A” record you created in the Prerequisite section.server { listen 80; server_name board.example.com; location ~ /ws/* { proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; client_max_body_size 50M; proxy_set_header Host $http_host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header X-Frame-Options SAMEORIGIN; proxy_buffers 256 16k; proxy_buffer_size 16k; client_body_timeout 60; send_timeout 300; lingering_timeout 5; proxy_connect_timeout 1d; proxy_send_timeout 1d; proxy_read_timeout 1d; proxy_pass http://localhost:8000; } location / { client_max_body_size 50M; proxy_set_header Connection ""; proxy_set_header Host $http_host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header X-Frame-Options SAMEORIGIN; proxy_buffers 256 16k; proxy_buffer_size 16k; proxy_read_timeout 600s; proxy_cache_revalidate on; proxy_cache_min_uses 2; proxy_cache_use_stale timeout; proxy_cache_lock on; proxy_http_version 1.1; proxy_pass http://localhost:8000; } } - Save and close the file.
- Test the Nginx configuration for errors.
$ sudo nginx -t - Restart Nginx.
$ sudo systemctl restart nginx
Configure the Firewall
- Allow HTTP port
80through the firewall.$ sudo firewall-cmd --permanent --add-port=80/tcp - Allow the HTTPS port
443.$ sudo firewall-cmd --permanent --add-port=443/tcp - Restart the Firewall to save changes.
$ sudo firewall-cmd --reload
Install a Let’s Encrypt TLS/SSL Certificate
- Install the EPEL repository.
$ sudo dnf install https://dl.fedoraproject.org/pub/epel/epel-release-latest-9.noarch.rpm - Install snap.
$ sudo dnf install snapd - Enable and start snap.
$ sudo systemctl enable snapd $ sudo systemctl start snapd - Install snap core, and create necessary links.
$ sudo snap install core $ sudo ln -s /var/lib/snapd/snap /snap $ sudo echo 'export PATH=$PATH:/var/lib/snapd/snap/bin' > /etc/profile.d/snap.sh - Install Certbot.
$ sudo snap install --classic certbot - Enable Certbot.
$ sudo ln -s /snap/bin/certbot /usr/bin/certbot - Request a Let’s Encrypt certificate. Replace
board.example.comwith the DNS “A” record you created in the Prerequisite section and make sure the webroot directory/usr/share/nginx/htmlis accessible.$ sudo certbot certonly --webroot -w /usr/share/nginx/html -d board.example.com - Edit the Nginx configuration file.
$ sudo nano /etc/nginx/conf.d/board.example.com - Paste the following configurations after the
listen 80;directive. Again, replaceboard.example.comwith your server name.listen 443 ssl http2; listen [::]:443 ssl http2; server_name board.example.com; # redirect all requests to https if ($scheme = http) { return 301 https://$server_name$request_uri; } ssl_certificate /etc/letsencrypt/live/board.example.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/board.example.com/privkey.pem; ssl_trusted_certificate /etc/letsencrypt/live/board.example.com/chain.pem; ssl_session_cache shared:SSL:1m; ssl_session_timeout 10m; ssl_ciphers PROFILE=SYSTEM; ssl_prefer_server_ciphers on; - Save and close the file.
Your completed Nginx configuration file should look similar to the one below, with your domain names.
server { listen 80; listen 443 ssl http2; listen [::]:443 ssl http2; server_name example.com; # redirect requests to https if ($scheme = http) { return 301 https://$server_name$request_uri; } ssl_certificate /etc/letsencrypt/live/example.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/example.com/privkey.pem; ssl_trusted_certificate /etc/letsencrypt/live/example.com/chain.pem; ssl_session_cache shared:SSL:1m; ssl_session_timeout 10m; ssl_ciphers PROFILE=SYSTEM; ssl_prefer_server_ciphers on; location ~ /ws/* { proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; client_max_body_size 50M; proxy_set_header Host $http_host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header X-Frame-Options SAMEORIGIN; proxy_buffers 256 16k; proxy_buffer_size 16k; client_body_timeout 60; send_timeout 300; lingering_timeout 5; proxy_connect_timeout 1d; proxy_send_timeout 1d; proxy_read_timeout 1d; proxy_pass 127.0.0.1:8000; } location / { client_max_body_size 50M; proxy_set_header Connection ""; proxy_set_header Host $http_host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header X-Frame-Options SAMEORIGIN; proxy_buffers 256 16k; proxy_buffer_size 16k; proxy_read_timeout 600s; proxy_cache_revalidate on; proxy_cache_min_uses 2; proxy_cache_use_stale timeout; proxy_cache_lock on; proxy_http_version 1.1; proxy_pass 127.0.0.1:8000; } } - Test Nginx for errors.
$ sudo nginx -t - Restart Nginx.
$ sudo systemctl restart nginx
Configure Focalboard as a System Service
- Create a new system service file.
$ sudo nano /lib/systemd/system/focalboard.service - Add the following contents to the file.
[Unit] Description=Focalboard [Service] Type=simple Restart=always ExecStart=./opt/focalboard/bin/focalboard-server WorkingDirectory=/opt/focalboard [Install] WantedBy=multi-user.target
Save the file.
- Restart the systemd daemon.
$ sudo systemctl daemon-reload - Enable the Focalboard service file.
$ sudo systemctl enable focalboard.service - Start Focalboard.
$ sudo systemctl start focalboard - Verify that Focalboard is running.
$ sudo systemctl status focalboard
Test Focalboard
Visit your server in a web browser.
https://board.example.com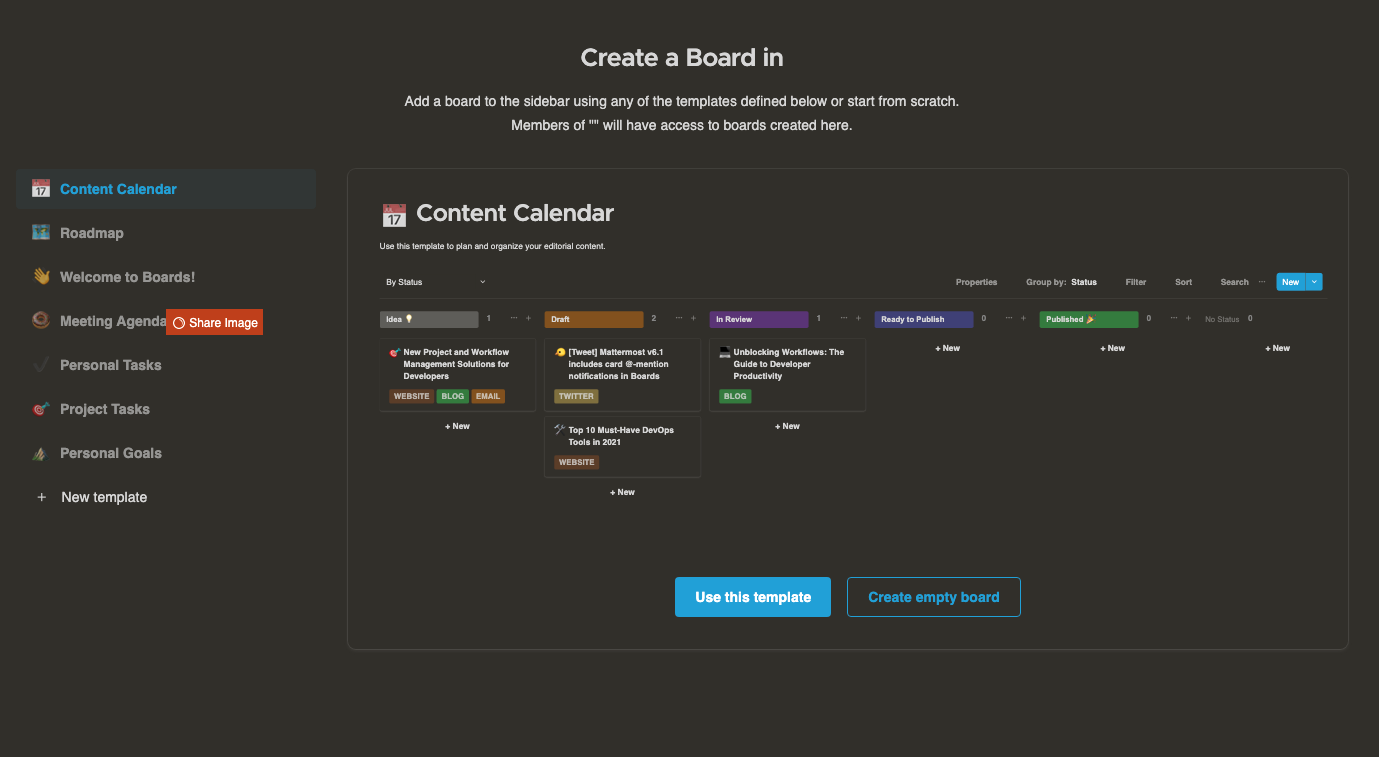
Create a new account and complete your Focalboard setup.
Introduction Focalboard is a free, open-source collaboration and productivity tool that lets you organize and manage projects. This article explains how to install Focalboard on a CentOS 9 Stream server. Prerequisites Launch a new CentOS 9 Stream server on Vultr. Create a DNS “A” record pointing to the server’s IP address, like board.example.com.…
Introduction Focalboard is a free, open-source collaboration and productivity tool that lets you organize and manage projects. This article explains how to install Focalboard on a CentOS 9 Stream server. Prerequisites Launch a new CentOS 9 Stream server on Vultr. Create a DNS “A” record pointing to the server’s IP address, like board.example.com.…